Android private DNS: What it is and how to enable it

Android offers a built-in security feature called private Domain Name System (DNS), which can enhance your online privacy by encrypting your DNS queries. Without secure DNS, your queries are left exposed for your internet service provider (ISP) or others on the network to collect.
This article explains what private DNS on Android is, why you should protect your DNS queries, and how you can fix basic DNS-related issues on Android.
What is private DNS on Android?
Private DNS on Android is a built-in feature introduced in Android 9 that encrypts domain‑name lookups using DNS‑over‑TLS (DoT). When enabled, your device sends DNS queries through an encrypted Transport Layer Security (TLS) connection to a specified resolver instead of sending unencrypted requests over the network. This shields the domain names you visit from casual monitoring.
This feature is available under your phone’s network settings and requires a hostname from your chosen DNS provider to work. By default, this feature is turned on and uses the DoT resolver provided by your current network. If you manually set a hostname, it will use that provider instead.
How private DNS works
Normally, your device sends queries through a DNS resolver, which translates human‑readable domain names into numerical IP addresses. By default, these queries travel unencrypted, allowing network operators or potential attackers to intercept and modify them.
Starting with Android 9, Google implemented DoT, which protects DNS queries inside the TLS protocol and sends them to the resolver over port 853. This prevents anyone on the same network from reading or altering the domain names you request.
Android offers two modes for private DNS: automatic mode encrypts your queries whenever possible, but will still send unencrypted data when connectivity fails, while strict mode requires you to enter a specific resolver hostname (such as one.one.one.one) and refuses to fall back if the server is unreachable.
Android private DNS vs. DoH vs. VPN with private DNS
Android’s private DNS is separate from DNS‑over‑HTTPS (DoH), which also encrypts DNS queries. Android’s DoT uses a dedicated port (853) and Android’s built-in DNS service. DoH, on the other hand, encrypts DNS queries by sending them inside regular HTTPS traffic over port 443, and is typically set up within individual browsers. Because Android uses DoT, all apps benefit from encrypted DNS at the system level without needing individual configuration.
However, apps that bundle their own DNS clients or use DoH may bypass system settings. Note that, if you use ExpressVPN on your Android device, you don’t need to worry about Private DNS or DoH. ExpressVPN doesn’t use DoH because it would route your DNS requests through third-party providers and could interfere with secure connections. To prevent this, it uses a special canary domain that tells browsers not to enable DoH automatically while the VPN is active. ExpressVPN encrypts all your traffic, including DNS queries, and resolves them through its own private, zero-knowledge DNS servers, keeping your DNS requests securely within the VPN tunnel. (That said, if you manually turn on DoH in your browser settings, ExpressVPN can’t override it.)
Key features of Android private DNS
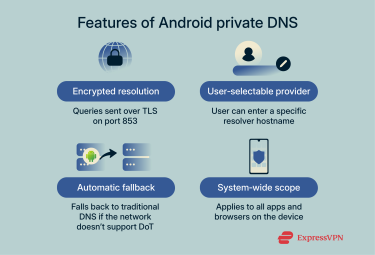
Private DNS on Android offers several features that enhance your privacy and security.
- Encrypted resolution: DNS queries are sent over TLS on port 853, which encrypts them and prevents eavesdropping.
- User-selectable provider: Android lets you enter a specific resolver hostname, meaning you can choose between providers such as Cloudflare, Google, or Quad9.
- Automatic fallback: In automatic mode, Android will try to upgrade your DNS traffic to DoT when the network supports it and fall back to traditional DNS if it doesn’t, ensuring connectivity even on networks without DoT support.
- System-wide scope: Once enabled, private DNS applies to all apps and browsers on the device, unless an app is configured to use its own resolver.
Why use private DNS on Android devices?
Enabling private DNS on your Android device ensures that domain name lookups are encrypted. It also lets you choose a trusted resolver with features like malware filtering and ad blocking, improving both your privacy and your device’s security.
Preventing ISP tracking
ISPs can monitor the domain names your device resolves because conventional DNS queries are sent unencrypted. By switching to private DNS, your device sends queries through a secure TLS tunnel, preventing ISPs from inspecting or logging the domain names you request.
Improving security and privacy
Private DNS contributes to your security by blocking eavesdropping and preventing DNS hijacking, where malicious actors intercept your queries and redirect you to fraudulent sites.
Choosing a resolver like Quad9 also adds threat‑blocking capabilities.
Does private DNS make browsing faster?
Switching to a reputable DNS provider through private DNS can reduce lookup latency because some providers, like Cloudflare and Google, operate global networks optimized for speed.
However, speed improvements depend on your location and network conditions. Private DNS simply allows you to choose a resolver that may be faster than your ISP’s option, rather than accelerating browsing by default.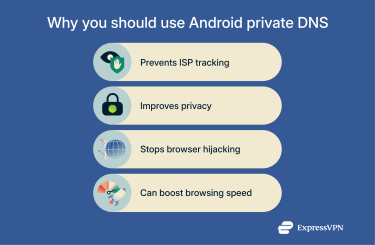
Limitations of private DNS on Android
While private DNS is helpful, it has some limitations. On its own, it isn’t a comprehensive privacy protection tool.
Private DNS vs. VPN: What it can and can’t do
It’s important to understand the distinction between Android’s private DNS feature and a full VPN. Private DNS focuses solely on encrypting DNS lookups; it doesn’t encrypt other types of data. Using private DNS on its own can only protect your queries from being traced.
By contrast, a VPN routes all your internet traffic through an encrypted tunnel and a remote server, encrypting all of your network traffic instead of just queries. A VPN also applies its own DNS resolver to prevent DNS leaks; ExpressVPN, for instance, runs its own private, encrypted DNS on every server, ensuring that your DNS queries never leave the encrypted tunnel.
However, alongside the added security, VPNs introduce extra encryption overhead, which can slightly reduce your connection speed. Fortunately, with a VPN optimized for speed, this decrease is minimal.
App-based tracking that DNS can’t block
Mobile apps can sometimes bypass DNS-level filtering, which results in your queries still being logged. These apps often use tracking libraries that communicate with analytics servers through encrypted HTTPS connections or with obfuscated requests. The result is that they can bypass DNS-level filtering altogether.
It’s also possible for an app developer to connect their app to specific resolvers, such as Cloudflare, and have all traffic be routed through that provider, bypassing your secure DNS. Some apps, like browsers, may incorporate their own encryption protocols, like DoT and DoH. When this happens, your traffic is routed through that app's secure tunnel.
How to enable and configure private DNS on Android
To use private DNS, your Android device must run version 9 or higher. Remember that if you’re using a quality VPN like ExpressVPN, your queries are automatically routed through secure DNS, so you don’t need to follow these steps.
- Open Settings and tap Network & Internet.
- Tap Private DNS.
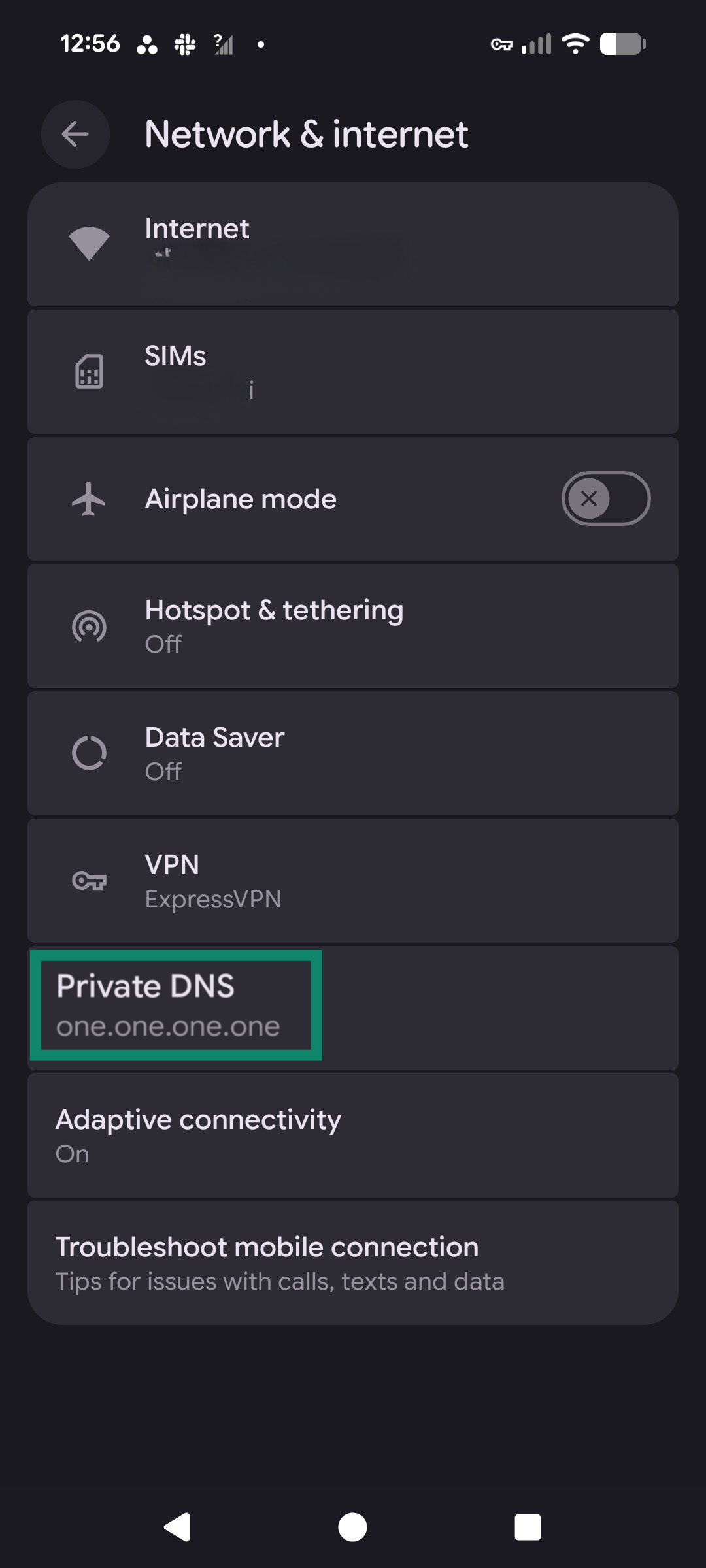
- Select Private DNS provider hostname. Enter a provider (e.g., dns.google or Cloudflare’s one.one.one.one).
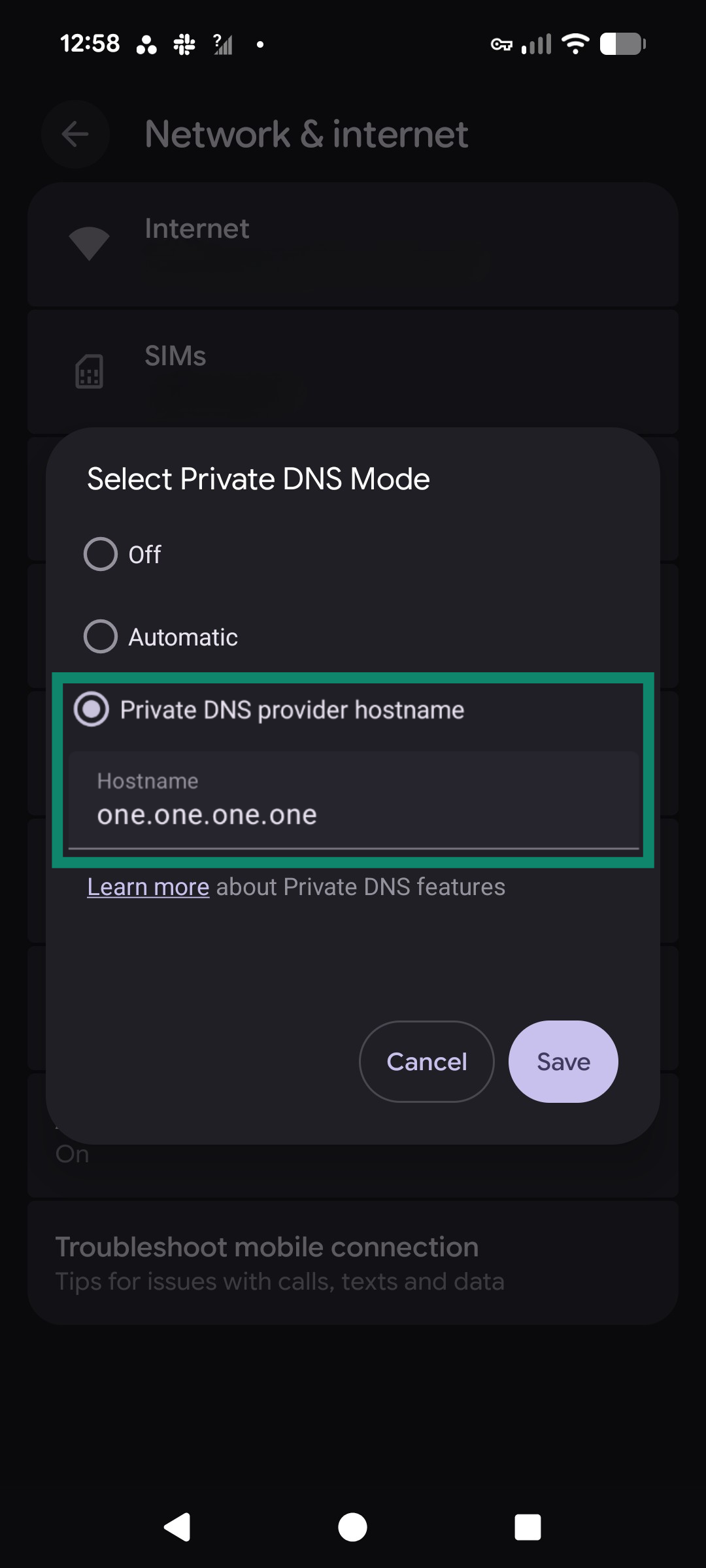
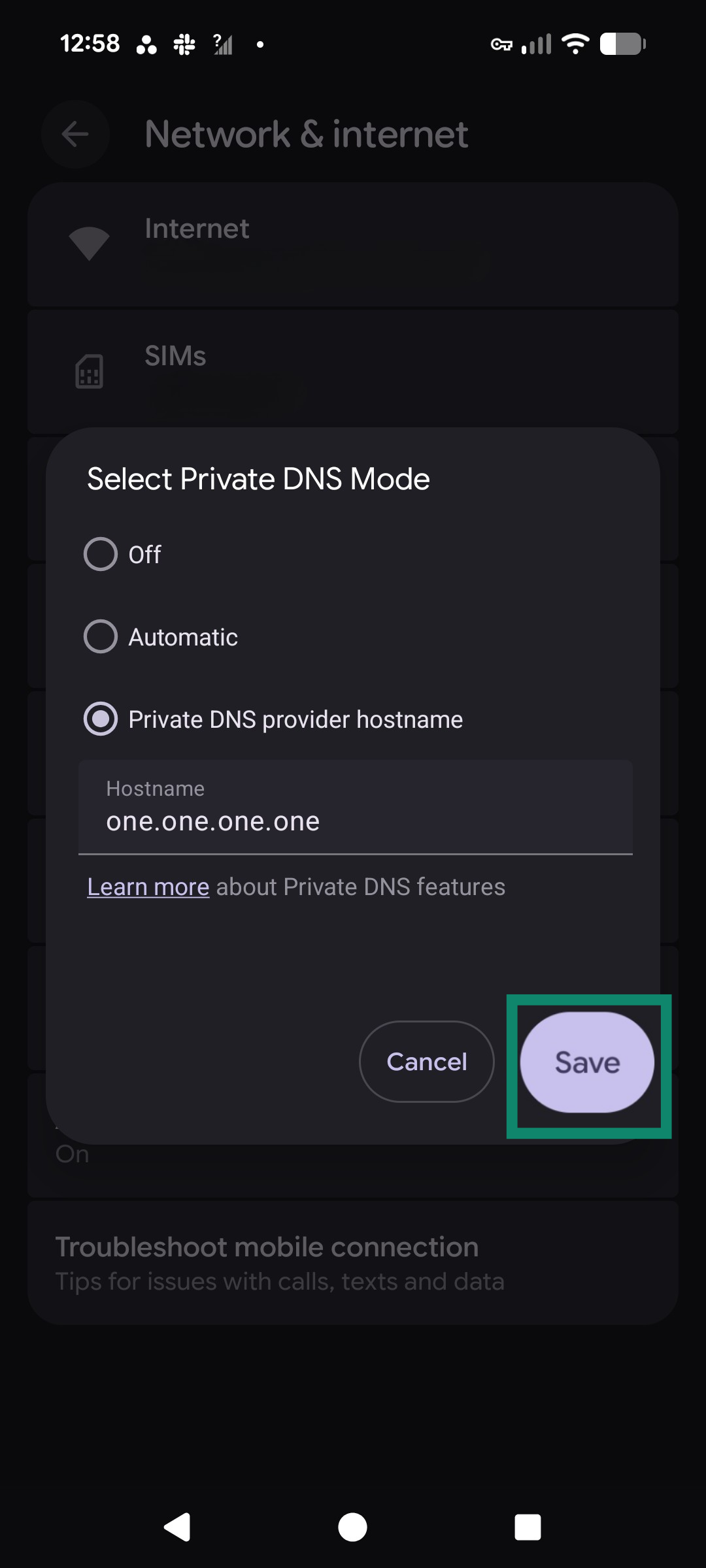
- Tap Save. Your DNS traffic is now encrypted.
Troubleshooting setup issues
If private DNS doesn’t work as expected, these steps can help resolve common problems:
- Verify hostname: Ensure you entered a fully qualified domain name for the resolver in your Private DNS menu. Using an IP address or misspelling the hostname will result in an error because DoT requires accurate hostnames to function. Compare what you’ve written with the official hostname for your DNS.
- Network compatibility: Test the connection on another network. Some public Wi‑Fi networks block DoT traffic, causing the “No internet access” warning.
- Switch to automatic: If strict mode fails, try selecting the automatic option to let Android fall back to unencrypted DNS. This can restore connectivity while still attempting data encryption whenever possible.
Note that these settings change dramatically if you’ve rooted your phone or loaded a new OS onto it.
Testing your private DNS configuration
To confirm that your Android device is using the desired resolver and that your DNS queries are encrypted, follow these steps:
- Online testers: Visit a DNS leak test website through your mobile browser. These tools report which resolver is handling your queries and whether they’re encrypted. If your DNS is leaking, you’ll get the same test results with and without your private DNS active.
- Restart device: After changing your DNS settings, restart your phone to ensure the new configuration is loaded. Then, test again.
- Use diagnostic apps: Some network tools for Android can verify the active DNS servers and the protocol in use. Running these tools can confirm whether the system is using DoT or falling back to regular DNS.
Fixing “Private DNS server cannot be accessed” error
When Android displays this error, it means the device can’t establish a TLS connection to the specified resolver. You can often fix this by following these steps:
- Check hostname accuracy: Double‑check that the entered hostname is correct. Typos or using an IP address instead of a hostname will prevent DoT from working.
- Change network or disable captive portals: Some networks block port 853. Try connecting to a different Wi‑Fi network. Expert users who have their developer options enabled can try temporarily disabling captive portal detection to see if the error persists.
- Switch modes: Open your phone’s DNS settings and set private DNS to either Automatic or Off, and see if connectivity returns. If your chosen provider’s server is down, this will let your device use the default DNS until the issue is resolved.

The best private DNS providers for Android
Several DNS providers stand out for Android users due to their performance, privacy commitments, and security features.
Popular free DNS providers
Cloudflare DNS (one.one.one.one)
Cloudflare’s one.one.one.one service is highly secure and has almost no downtime. As part of its privacy commitment, the company does not log IP addresses; it anonymizes them and then deletes logs within 25 hours.
Cloudflare offers robust DoT and DoH support, and its global network helps deliver low‑latency responses worldwide. It supports Domain Name System Security Extensions (DNSSEC) validation, but it lacks content filtering.
Google DNS (8.8.8.8)
Google Public DNS is widely available and well supported, offering DoT and DoH encryption. Google collects aggregate data to improve performance, but states that it doesn’t permanently store personally identifiable information and doesn’t share personal data with the purpose of ad targeting.
Google DNS is known for its stability and broad reach. It provides extra security features, including DNSSEC validation, though it lacks malicious content filtering.
OpenDNS
OpenDNS provides free resolvers (208.67.222.222 and 208.67.220.220) and supports filtering categories such as adult content or phishing. It offers DoH and DoT through the hostname dns.opendns.com, though some features require you to open a free account.
OpenDNS stores limited logs for security and troubleshooting, but has transparent data retention policies and supports DNSSEC validation to protect against spoofing. However, OpenDNS requires manual configuration on Android, so it’s less convenient for most users.
Quad9 DNS
Quad9 is a nonprofit DNS provider that integrates threat intelligence from multiple sources to protect your privacy and block malicious domains.
It doesn’t collect personal data or store client IP addresses, and it uses encryption protocols such as DoT, DoH, and DNSCrypt to protect your queries. Logs are aggregated for performance analysis but are anonymized and not associated with specific individuals. To use Quad9 on Android, enter dns.quad9.net as the private DNS hostname.
Use ExpressVPN’s private DNS
ExpressVPN offers a private, zero‑knowledge DNS service that operates inside its VPN tunnel. All of ExpressVPN's servers use secure DNS, and when you connect to it, your DNS queries are handled by ExpressVPN’s own resolvers, ensuring they remain encrypted and are never logged or shared.
FAQ: Common questions about Android private DNS
Should I turn on private DNS on Android?
Android’s private Domain Name System (DNS) is an on-by-default feature that improves your privacy and security. It encrypts DNS queries and allows you to choose a resolver with extra security features, including malware filtering, for example. Because the feature is lightweight and free to use, there’s little downside unless you connect to a network that blocks private DNS traffic.
Is private DNS the same as a VPN?
Private Domain Name System (DNS) encrypts only domain name lookups, whereas a VPN encrypts all your internet traffic and masks your IP address. Some VPNs, like ExpressVPN, use private DNS on every server, meaning you get the benefits of secure DNS and full network encryption at the same time.
How can I check if private DNS is enabled?
You can verify private Domain Name System (DNS) by visiting a DNS leak test website like ExpressVPN’s, which will show the resolver handling your queries. Run a test without your secure DNS active, and then run a test with it active. If it works, you won’t see the same results.
What happens if I turn off private DNS?
When you disable private Domain Name System (DNS), your device reverts to using unencrypted DNS queries. This exposes your domain requests to your internet service provider (ISP) or anyone with access to your connection. Turning it off may restore connectivity on networks that block DNS‑over‑TLS (DoT) traffic, but you lose the encrypted DNS benefit.
What should my DNS settings be?
The best Domain Name System (DNS) settings depend on your priorities. If you want the fastest response times, Cloudflare and Google are free to use and are widely considered secure. However, for enhanced privacy protection, consider a tool like Quad9 DNS or a secure VPN to encrypt all of your data, including your DNS queries.
Are there risks in using free DNS services?
Free Domain Name System (DNS) providers may collect or retain data for analytics or share it with third parties. Always review the provider’s privacy policy and choose well‑known, transparent services like Cloudflare.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN